What are Passkeys?
Can we finally get rid of usernames and passwords?
The TL;DR
Passkeys are a way to securely sign into the apps and websites you love without needing to remember a password or username.
Passwords have been around since the 60’s, and are both not-that-secure and annoying to remember and manage
Passkeys – based on public/private cryptography – let you log in instantly and securely without having to manage usernames and passwords
Passkeys are picking up momentum: companies like Adobe, Kayak, and PayPal support logging in with them
As the developer of an app or site though, it’s tedious and difficult to implement Passkeys yourself across browsers and devices
The Passkey technology has been around for a while, but 2023 has been a critically important year, thanks to some important releases from Google and Apple. So read on!
Passwords are not a good time
Unless you’re stuck trying the 13th combination of letters and numbers for the random account you haven’t logged into in 4 years, you probably don’t often consider whether the entire concept of passwords is a good one or not. The idea of a password for a computer was first introduced in 1960 at MIT, and the general scheme has stayed roughly the same. But the internet has changed a lot since then, and it’s starting to become clearer that passwords aren’t working:
Passwords make for a poor user experience
Maintaining a separate username and password for every internet service you want to sign into is obviously not an ideal experience. Password managers like 1Password make this a good deal easier, but only 1 in 3 Americans is actually using one. The rest are either memorizing unique username/password combinations for each service, storing them in a spreadsheet, or worse: using the same username and password for multiple accounts. Which brings us to the second important point about passwords…
Passwords are inherently hackable
Virtually every major breach in the past 10 years has involved, in one way or another, someone gaining access to an account fraudulently. Passwords are phishable, they can get leaked, they’re stored on someone else’s servers…the list goes on. People are even having success with hacking passwords using AI.
Passwords not being the most secure thing in the world isn’t exactly news. Over the past few years, you’ve probably seen more and more services offer MFA, or Multi-Factor Authentication. MFA uses a method other than your password to double-verify that you are who you say you are, usually in the form of an SMS, Email, or Authentication app like Authy. That way, if your password gets leaked, a hacker would still need to have access to other pieces of your identity (phone, email, etc.) to log in.
MFA definitely helps you lock down your accounts, but it’s also annoying and time consuming. This is usually a tru-ism in general: there’s a tradeoff between security and user experience. Want to make something more secure? It’s going to have to be harder to use. Want to make something easier to use? It’s likely going to be less secure.
Passkeys in theory: public key encryption
The cool thing about Passkeys is that they’re both more secure and easier to use than passwords. The technology is based on public key encryption, which has been around since the 70’s. There’s no shortage of videos on the web explaining this concept in depth, so I’ll keep it simple.
Everything starts with a problem: how do you share something with someone securely, and make sure no unauthorized people get access to it? Way back in the early 1970’s, a few researchers figured out a clever way to get this done over the internet. Everyone gets two “keys” or pieces of identification:
Your public key: it’s unique to you, and everyone has access to it.
Your private key: it’s unique to you, and only you have access to it.
If someone wants to send a message to you (and only you), they’ll “lock” the message with your public key (remember, everyone has access to that). But only your private key can “unlock” something locked with your public key, so nobody else can access it. You can almost think of your public key as a locked door that anyone can put things behind, but only you can access those things. This process is classically explained with two people named Alice and Bob (boring):
Passkeys take this public key encryption concept and apply it to logging into services on the web. If you think of your account as the “message” – the provider will sign it with your public key, and only you can log in, using your private key. Think of Peter as Google, Lumbergh as you, and the message as access to your Google account.
🔍 Deeper Look 🔍
In practice by the way, these “keys” are just really long, meaningless strings of letters and numbers stored on your computer, phone, etc.
🔍 Deeper Look 🔍
Because your private key is stored on your device, you don’t need to remember or store any passwords. All you need to do is prove that you are the owner of your device – which on laptops and phones today is as simple as TouchID, FaceID, or any other quick biometric option. It’s important to stress that with Passkeys, it’s not your fingerprint or face that’s actually doing the authentication; it’s just proving that you own your device. It’s the private key that’s on that device where the magic is happening.
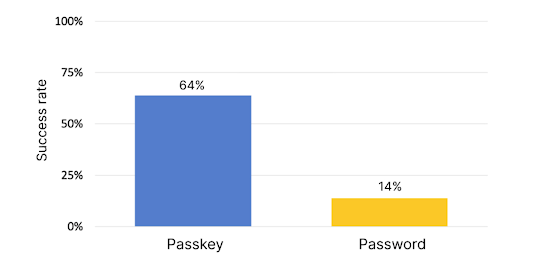
And the proof is in the Passkeys. Research from Google showed that in addition to Passkeys being up to 2x faster than passwords, they’re also more reliable; only 14% of first attempts to sign in with a password were successful, compared to 64% for Passkeys.
Let’s get into how they work in practice.
Passage by 1Password helps you implement passkeys – a more secure and 2x faster sign-in experience than passwords – in your app with just a few lines of code. Get cross-platform, ready for production authentication in minutes. Technically readers get an exclusive six-month free trial with the code ‘TECHNICALLY6MO’!
<passage-auth app-id=[PASSAGE-APP-ID]></passage-auth>
<script src="https://psg.so/web.js></script>Passkeys in practice: Google and you
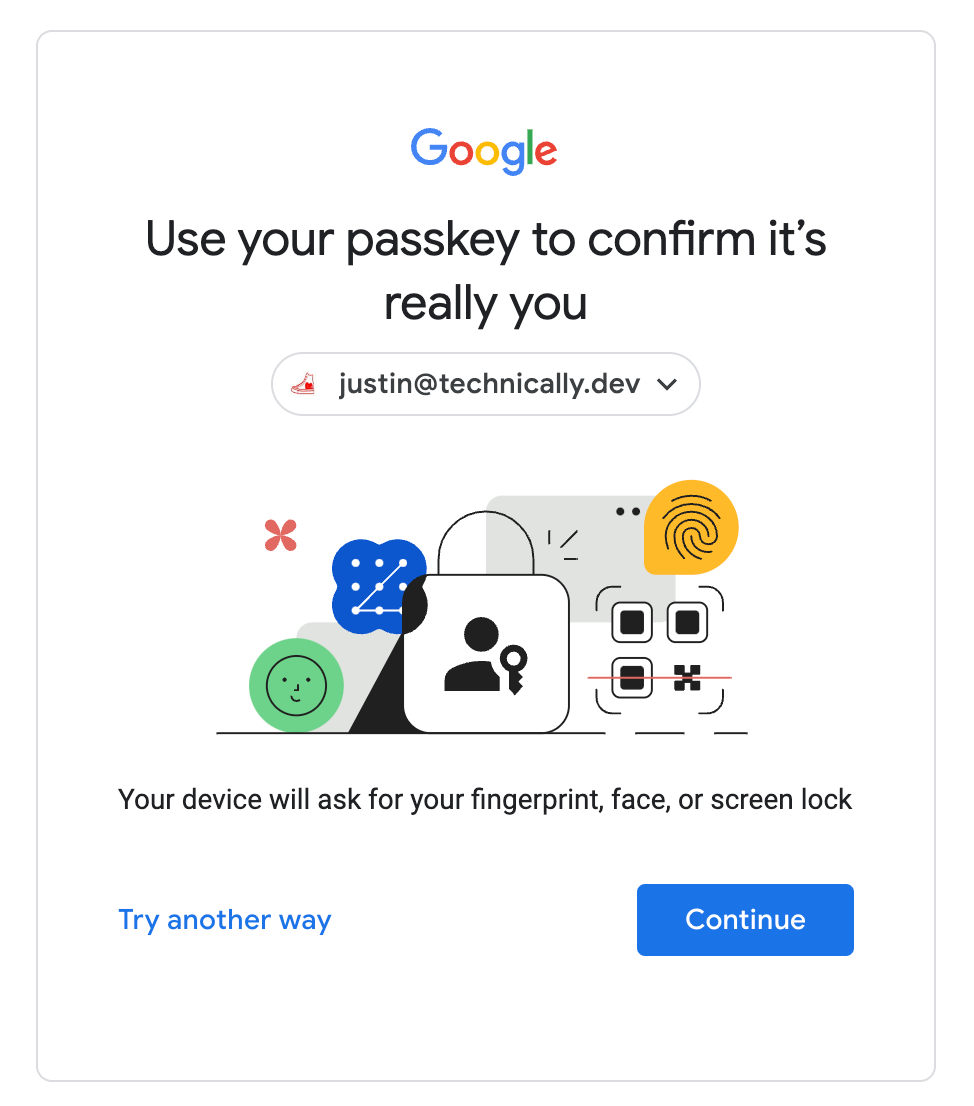
Google has been one of the early movers in the Passkey space, and as of May of this year, you can log into Google services using Passkeys. Once you create a Passkey, signing in is as simple as going to your login screen:
And selecting Passkey as your authentication mechanism:
My Macbook Pro prompted me for my fingerprint to verify that I have access to the device, and then that was it. No passwords to remember, and virtually unhackable.
If the Passkey tech has existed for a while now, and it seems so dope, why has it taken this long for it to become a legitimate way to sign into services on the web? The short answer is that the complexity is in managing Passkeys, especially across devices.
How do you sign into the same account from different devices?
Do you need a separate Passkey for each one?
What happens when you get a new phone, or switch laptops?
This is why things have picked up recently. Google and Apple, who both happen to own (a) the biggest browsers in the world and (b) the biggest cloud identity services in the world (Drive and iCloud) have been investing in Passkey technology big time. They’ve added support for syncing Passkeys across your devices, at first using their native password managers, but now also with third-party ones like 1Password.
These reasons are also why it’s so hard to implement Passkeys as a provider. If you’re a developer who wants to let your users sign in via Passkeys, you need to worry about a lot:
Complete implementation differences across browsers and devices (e.g. Passkeys don’t seem to work pre-iOS 14, iOS is completely different than Android, etc.)
Handling Passkeys across multiple devices
Handling account recovery
Providing password-less fallback options (like Magic Links)
Constant updates from platforms (like Chrome) and keeping up with them
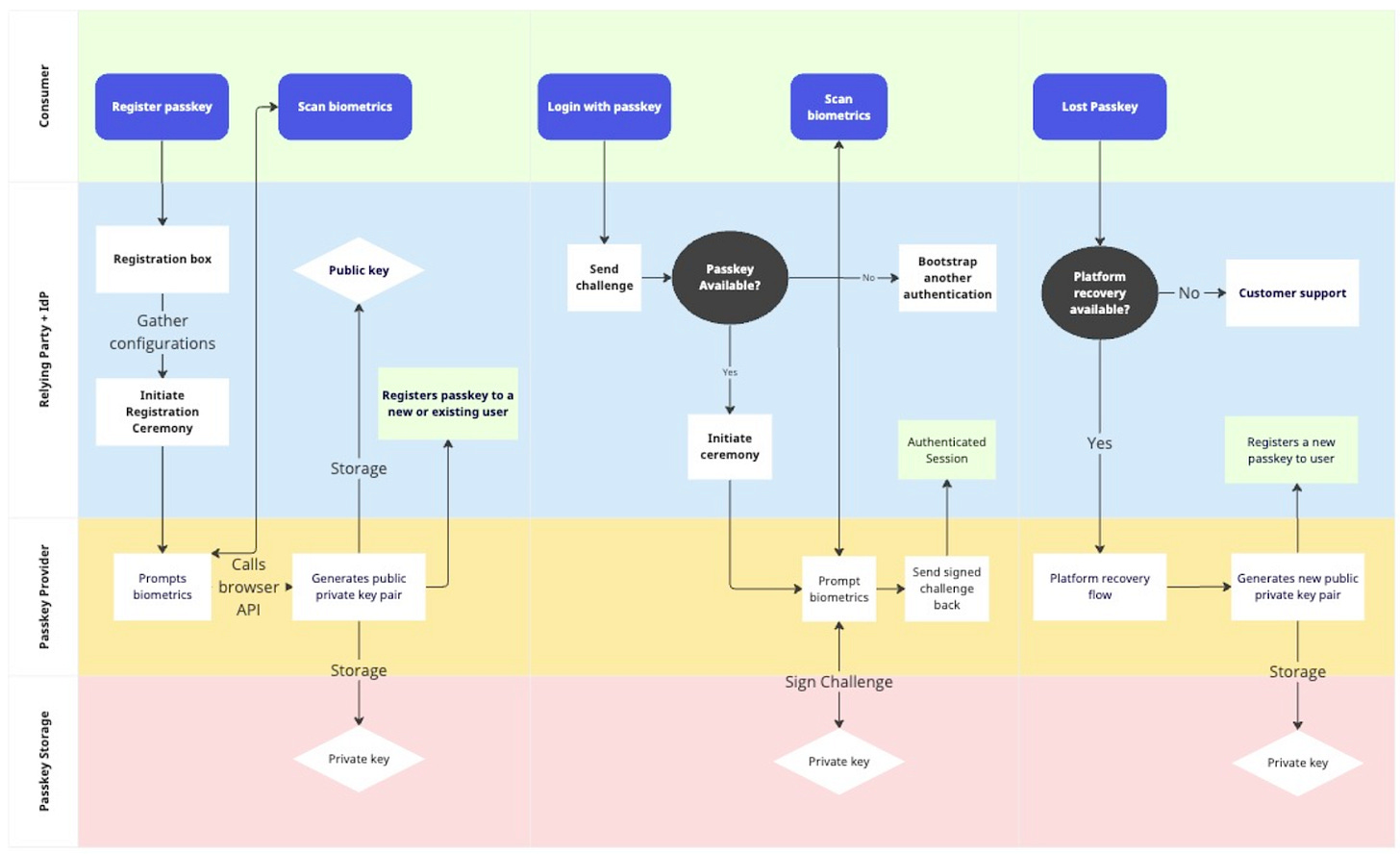
Here’s a sample diagram of what implementing one of these flows yourself might look like. Don’t worry too much about the specifics; the idea is that it’s a lot more complicated than you might think.
The underlying APIs for Passkeys today are under an umbrella called WebAuthn. There’s an emerging ecosystem of libraries and tools to make working with the protocol easier, but it’s still early. 1Password’s new developer-focused product (called Passage) helps avoid a lot of these headaches and lets developers implement Passkeys with just a few lines of code.
We are getting there though! Several major brands now support authentication via Passkeys, like Tiktok, WhatsApp, Instacart, eBay, PayPal, and many more. You can find a directory of services that provide Passkey authentication here. If you want to get started with Passkeys, check the directory and see if any of the services you use support them. Google is always a good place to start, although if you’re trying to enable Passkeys on your work account, your GSuite Admin will need to authorize them first.
Passage by 1Password helps you implement passkeys – a more secure and 2x faster sign-in experience than passwords – in your app with just a few lines of code. Get cross-platform, ready for production authentication in minutes. Technically readers get an exclusive six-month free trial with the code ‘TECHNICALLY6MO’!
<passage-auth app-id=[PASSAGE-APP-ID]></passage-auth>
<script src="https://psg.so/web.js></script>







Are you telling me that passwordless authentication is a misnomer :).
This was a super thoughtful and helpful post. Justin what do you think of KeyFactor and Venafi and some of the third party passkey companies. What is PKI and cloud PKI and will Google and Apple crush the system by using their own technology?